Beauty company Estée Lauder with a revenue of USD 17.4 billion has become a victim of separate ransomware attacks by the ALPHV/BlackCat and Clop gangs.
In a Security Exchange Commission (SEC) filing, Estée Lauder confirmed one of the attacks, stating that the threat actor gained access to some systems and potentially stole data. It’s believed that the Clop ransomware group exploited a vulnerability in the MOVEit Transfer platform to breach the company, listing Estée Lauder on their data leak site with a message criticizing their lack of concern for customer security, noting that they have stolen more than 131GB of the company’s data.
The Active Protection included in Acronis Cyber Protect detects and blocks ransomware from Clop, BlackCat and other groups, keeping your data safe from encryption or extortion.
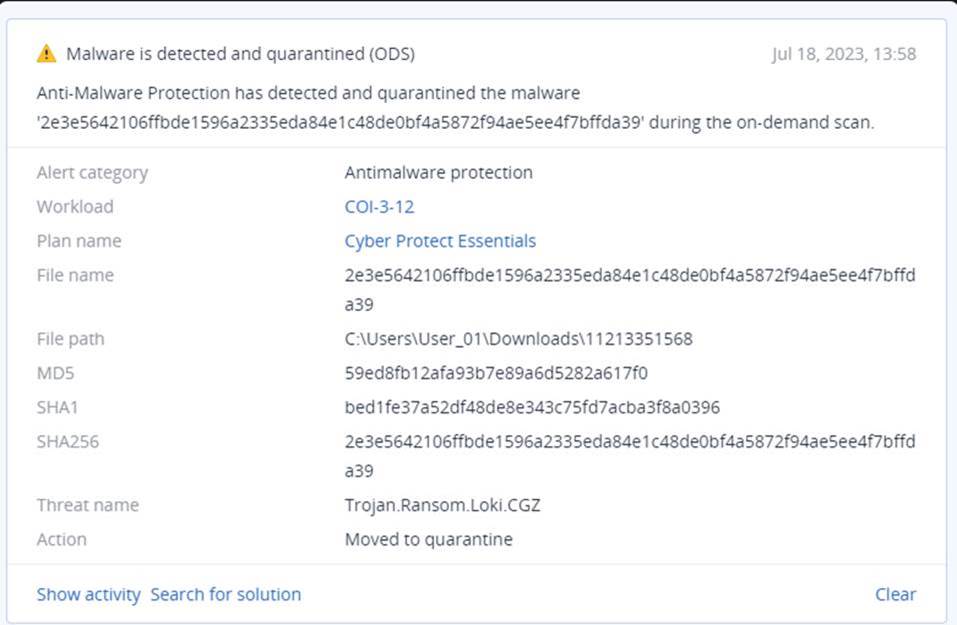
Phishing attacks employing Microsoft Word documents have been discovered to drop the information-stealing Trojan LokiBot on compromised systems. LokiBot, also known as Loki PWS, has been active since 2015 and primarily targets Windows systems to extract sensitive information from infected machines.
Researchers have spotted a campaign that exploits two known vulnerabilities, CVE-2021-40444 and CVE-2022-30190 (aka Follina), to achieve code execution. In one attack vector, a Word file exploits CVE-2021-40444 to download an HTML file that leverages Follina to deliver a Visual Basic injector module, which decrypts and activates LokiBot while employing evasion techniques to detect debuggers and virtualized environments.
Another attack chain incorporates a VBA script in a Word document to execute a macro that downloads an interim payload from a remote server, acting as an injector to load LokiBot. The malware boasts various capabilities, including logging keystrokes, capturing screenshots, stealing login credentials from web browsers, and siphoning data from cryptocurrency wallets.
Acronis Cyber Protect’s Advanced Email Security detects malicious & phishing emails and filters them automatically before they can do any damage. The AI-Powered and Behavioral Detection Engines in Acronis Cyber Protect detect and block malware on your computers, keeping them safe from threats and protecting your data.