By Merium Khalid, Director, SOC Offensive Security, Barracuda XDR
In 2023, Barracuda XDR, including its team of SOC analysts on 24-hour watch, cut through nearly two trillion (1,640 billion) IT events to isolate tens of thousands of potentially high-risk security threats.
Security researchers have analyzed the most prevalent XDR detections for 2023. Their findings, summarized in this blog, show the most common ways attackers tried — and failed — to gain persistent access to networks through intruder activity, such as business email compromise and using malicious code and exploits.
It’s important to note that defensive security technologies, including XDR, are designed to detect, notify, and block the enemy at the gate or in the early stages of an intrusion. The attacks are prevented from being carried out fully — and this means that we don’t always know what the final intended payload might have been, such as ransomware.
Overview of 2023: High-severity attack attempts increasing
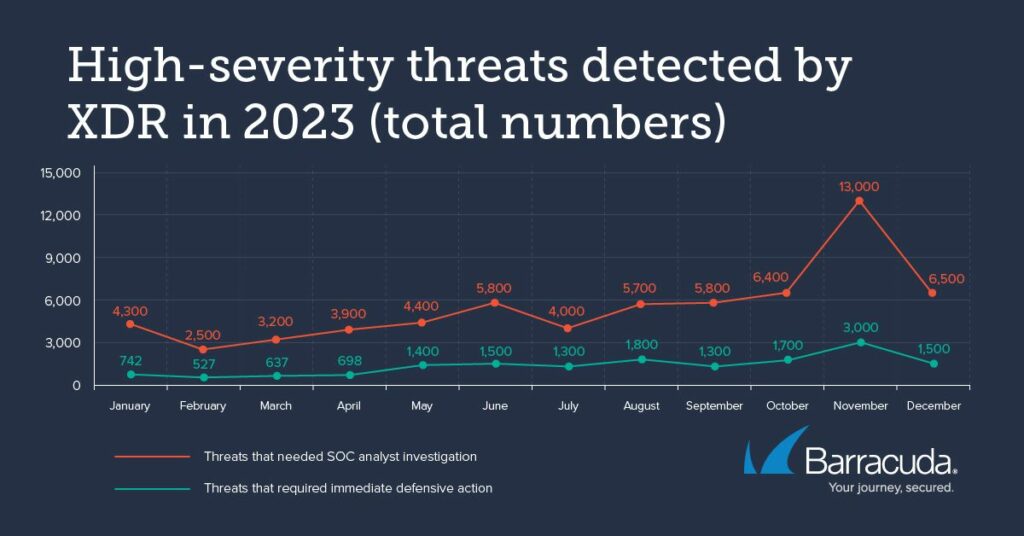
High-severity detections during 2023 included 66,000 threats serious enough to be escalated to a SOC analyst for investigation, and a further 15,000 that required urgent and immediate defensive action. There was a steady rise in both threat categories throughout the year — peaking from October into November and December.
These months are the prime season for online shopping and festive holidays. Both factors are potentially highly attractive to attackers. The first because it offers a large pool of potential targets and opportunities, the second because it generally means IT teams are away from the workplace or less attentive.
There was a second, smaller, peak in June — which for many countries represents a key holiday month.
Together, these results reinforce the findings we first reported in 2022 — that attackers seize the opportunity of people being away, busy, or distracted to launch more damaging and high-risk attacks.
Top XDR detections in 2023 center on identity abuse
The majority of the top 10 detections of 2023 are focused on some kind of identity compromise, resulting in a breached account. The detections that signpost this identity abuse include suspicious logins, brute force attacks, and attackers disabling multifactor authentication.
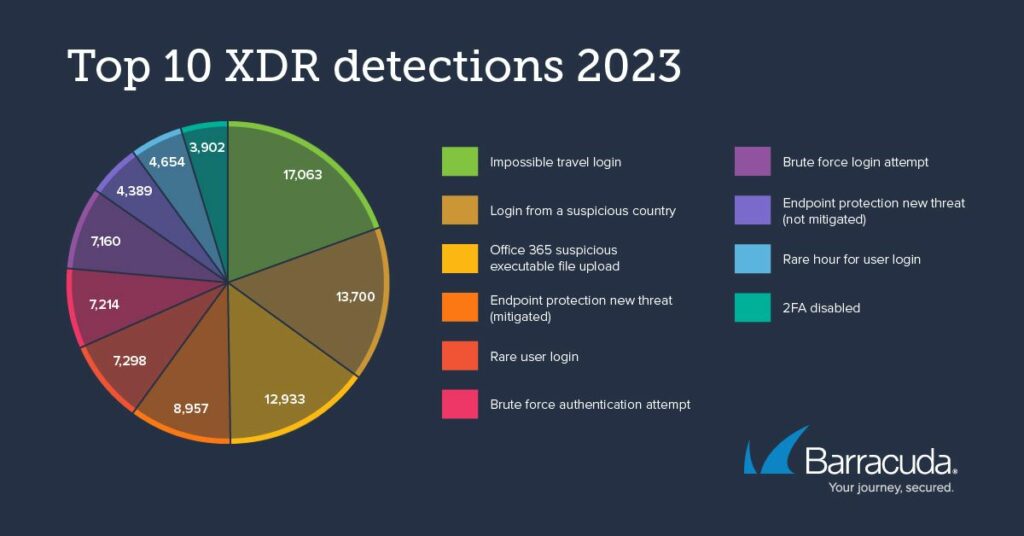
N= 87,720
The uploading of a suspicious executable file could indicate attackers trying to move additional tools or malware from an external, adversary-controlled system such as a command-and-control server into a compromised account.
Endpoint threat detections involve a mechanism that triggers when Barracuda’s Managed XDR Endpoint Security spots a potential threat within a system, regardless of whether it successfully neutralized the threat or not. It’s crucial to promptly notify the client in either scenario, as such detections necessitate a deeper investigation to uncover how the malicious file or process managed to execute initially.
This detection rule covers a wide spectrum of threats, including but not limited to harmless elements, potentially unwanted applications (PUA), adware, spyware, downloaders, cryptominers, malicious documents, exploits, viruses, worms, Trojans, backdoors, rootkits, information stealers, ransomware, interactive or remote shells, lateral movements, and more. Each category requires a tailored approach for effective identification and mitigation.
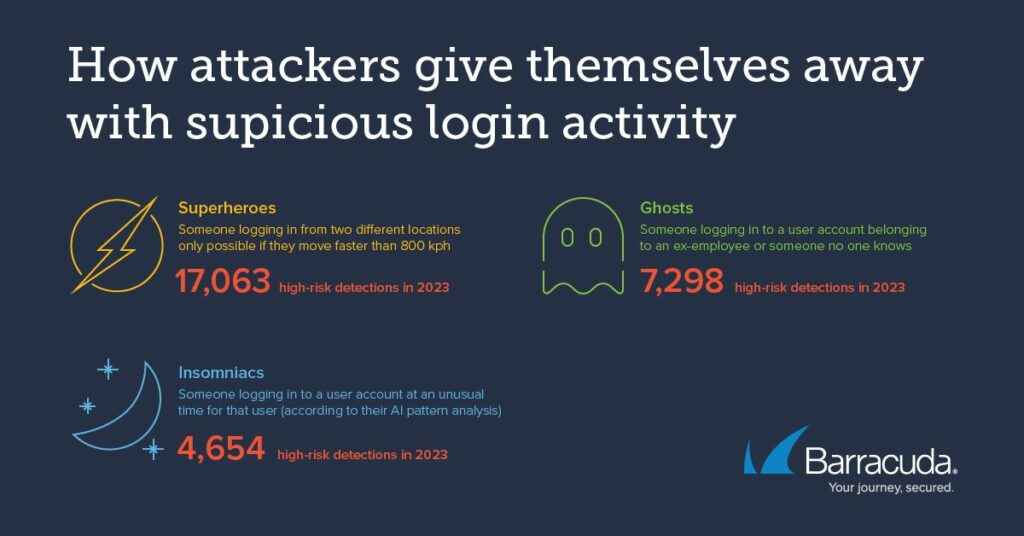
Suspicious superheroes, ghosts, and insomniacs — how AI tools spot intruders
Barracuda XDR features AI-powered detection rules, driven by our machine learning capabilities, designed to spot suspicious login activity that needs urgent evaluation. The rules rely on algorithms and AI-based pattern analysis, which model a user’s baseline routine and immediately red flag anything that falls outside that.
Suspicious superheroes — Impossible Travel detection rule
This detection rule catches attackers trying to log into a compromised account. When two logins are detected more than 1,000 km apart and the user would need to be travelling at more than 800 km/h — the average speed of an airplane — in order to do this, a security red flag is triggered. Furthermore, the detection checks the login isn’t associated with a VPN IP to remove any risk of a false positive.
To illustrate how this looks in practice, in one instance Barracuda XDR spotted a user logging in from Iowa in the U.S. and then in Moscow just over an hour later, seemingly covering 8,267 km at a speed of more than 7,000 km/hour.
Ghosts — Rare User Log-in detection rule
This detection rule looks for unusual usernames appearing in the authentication logs. This helps to spot an intruder abusing the credentials for a dormant or inactive user, perhaps because the user has left the organization, or a username that falls out of the organization naming schema. Threat actors will also try to create new users as a means of persistence, and this will be flagged as an unknown user by the detection rule.
Insomniacs — Rare Hour for User detection rule
This detection rule looks for a user logging in at a time of day that is unusual for them. This can be due to someone in a different time zone trying to access the compromised account. In addition, unauthorized user activity often takes place outside standard business hours.
Network traffic detections
Barracuda XDR includes a sophisticated, multilayered Intrusion Detection System (IDS) that scrutinizes traffic traversing a client’s network via a SPAN (mirror) port. This IDS serves as a vigilant guardian, pinpointing both suspicious and potentially harmful activities that might appear legitimate but are linked to recognized malware, cyberattacks, and various security threats permeating your network. A significant portion of these threats are automated, executed en masse against networks.
Analysis of the leading IDS detections in 2023 reveals a persistent trend: Attackers consistently exploit longstanding critical vulnerabilities and weaknesses that have yet to be addressed through patching. This highlights the critical need for continuous vigilance and updates to network security measures.
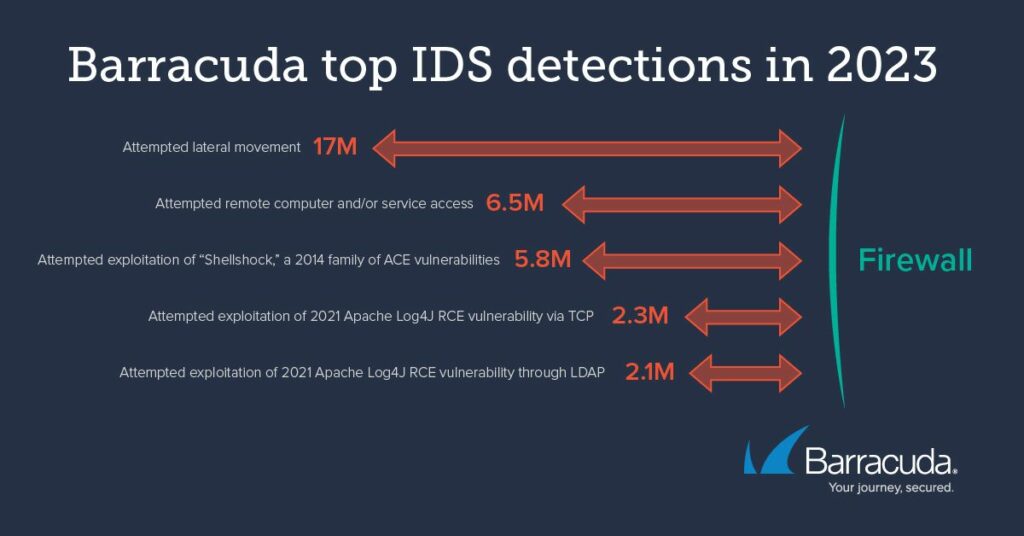
Shellshock is a 10-year-old collection of bugs that continues to rank among the top 10 detections detected by Barracuda’s integrated IDS. The fact that Shellshock attacks remain so prevalent suggests that attackers know there are still many unpatched systems out there. Reports suggest that Shellshock is being used by attackers to launch distributed denial of service (DDoS) attacks and to target vulnerable interconnected systems that are interconnected using bots and botnets.
Two years after the Log4Shell vulnerability in the open-source Java-based Log4j logging utility was disclosed, exploits against the bug also remain common. This could reflect the fact that Log4j is so deeply embedded in applications and other software that many organizations may not even know it is there — and vulnerable instances could be tricky and time-consuming to mitigate.
How to stay safe in a world of 24/7 attacks
The security basics are more critical than ever. These should include robust authentication and access controls (multifactor authentication at a minimum and ideally moving to Zero Trust- based measures), a solid approach to patch management and data protection, and regular cybersecurity awareness training for employees.
However, in the face of a growing number of high-severity threats targeting an organization’s expanding digital attack surface, and as attackers increasingly start to leverage AI for ever more sophisticated, faster, and targeted attacks, defenders will need to ensure their security tools have the same power. A multi-faceted, AI-based approach to protection that has several levels of increasingly deep detection and scrutiny is essential.
This should sit within an overall security framework that comprises robust next-generation security technologies, backed by expert analysis and 24/7/365 security monitoring to catch unknowns and anomalies that might otherwise slip through the net — and a SOC as a service to respond to and mitigate threats.
If you don’t have the time or expertise in-house, a managed XDR service that includes a SOC as a service can keep watch over every corner of your IT environment for you, all day, every day.
The findings are based on detection data from Barracuda Managed XDR, an extended visibility, detection, and response (XDR) platform, backed by a 24×7 security operations center (SOC) that provides customers with round-the-clock human and AI-led threat detection, analysis, incident response, and mitigation services.







