In the first half of 2022, FortiGuard Labs observed an overall increase in attack frequency paired with the explosive growth of new variants associated with familiar tactics. While attack volume isn’t showing any signs of slowing, the back half of the year gave rise to some other distinct trends in activity. For starters, our team witnessed destructive wiper malware attacks impacting more organizations across the globe, as well as enterprising cybercriminals reimagining existing botnets and reusing code to power new—and more sophisticated—attacks.
In our 2H 2022 Threat Landscape Report, we examine the cyber-threat landscape over the year’s second half to identify trends and offer insights on what security professionals should know to effectively protect their organizations in the new year and beyond. The report findings are based on the collective intelligence of FortiGuard Labs, drawn from Fortinet’s vast array of sensors collecting billions of threat events observed around the world during this same period. Below are key takeaways from the report.
2H 2022 Threat Report: A Summary
We’re increasingly seeing cybercriminals take a “work smarter, not harder” approach to unveiling new tactics. From new advanced persistent cybercrime tactics to upgrading old-school botnets like Mirai, bad actors continually find more sophisticated ways to infiltrate networks, making every organization regardless of size or industry a target.
APT-Like Wiper Malware Expands Worldwide
In the first half of the year, we saw a resurgence in wiper malware and, as we predicted, this destructive attack playbook has only widened its foothold during the second half of 2022. Wiper malware expanded into other countries, driving a 53% increase in wiper activity from Q3 to Q4.
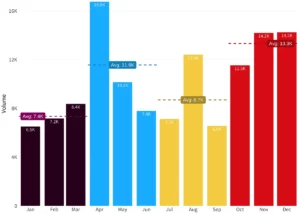
While we initially observed wiper malware being developed and deployed by nation-state actors—particularly in parallel with the Russia-Ukraine war—we’re now seeing wipers being scaled and deployed worldwide. These new strains are increasingly being picked up by cybercriminal groups and used throughout the growing Cybercrime-as-a-Service (CaaS) network. Cybercriminals are also now developing their own wiper malware which is being used readily across CaaS organizations, meaning that the threat of wiper malware is more widespread than ever and all organizations are a potential target, not just those based in Ukraine or surrounding countries.
Attackers Are Reimagining Old-School Tactics
Bad actors always seek to maximize their existing investments and knowledge in attack efforts. Botnet and malware code reuse are efficient, cost-effective ways for criminals to build upon successful attack vectors while making iterative changes, fine-tuning their attacks to sidestep detection.
Similar to musicians who remix chart-topping songs, cybercriminals are reimagining old attack strains that proved successful in the past and reintroducing new and enhanced versions. In the second half of 2022, we witnessed the resurgence of familiar names among botnets and malware variants, many of which are more than a year old.
For example, when examining botnet threats by prevalence, many of the top botnets are older. Mirai and Gh0st RAT continue to be popular across all regions, yet out of the top five, only RotaJakiro is from the current decade. While there are several new bots on the block, like RaspberryRobin, we’re observing an interesting rise in attackers’ reliance on established threats.
We saw a similar trend with malware. Some top strains observed in 2H 2022 such as Lazarus—which originated in 2010—are household names in cyber history. We also examined a collection of different Emotet variants to analyze their tendency to borrow code from one another. Our research showed that cybercriminals continue creating spinoffs of Emotet, with new variants breaking into roughly six different “species” of malware.
Although it may be tempting to write off older threats as history, these anecdotes are a reminder that organizations across all sectors need to remain vigilant. Code reuse and retrofitting—fueled by a growing CaaS ecosystem—underscores the importance of using comprehensive, consolidated security services powered by automation to counter threats.
Ransomware Remains at Peak Levels
Ransomware remains in full force, with cybercriminals constantly introducing new variants, largely thanks to the proliferation of Ransomware-as-a-Service (RaaS). In the second half of 2022, the top five ransomware families accounted for roughly 37% of all ransomware. GandCrab, a RaaS malware introduced in 2018, topped the list.
Despite the threat actors behind GandCrab announcing that they were retiring, there were many iterations of GandCrab created during its heyday. There may still be a long tail of variants coming from this operation, which makes the work of groups like The Cybercrime Atlas Initiative essential as they aim to dismantle these large-scale criminal operations permanently.
Drive-By Compromise Goes Full Throttle
Analyzing cybercriminal tactics and techniques gives us better insight into how to protect against future attack scenarios. In the second half of 2022, drive-by compromise topped the list across all regions as the most common malware delivery approach. This method involves attackers gaining access to victims’ systems while browsing online and getting them to download malicious payloads.
Organizations should regularly patch software and use intrusion prevention system (IPS) technology to counter this popular malware delivery method. Implementing ongoing cyber-awareness training programs for employees is also critical, as end-users are typically the first line of defense against a cyberattack.
Protect Your Organization Against the Evolving Threat Landscape
As organizations’ cyber defenses are improving, bad actors have their work cut out for them as they attempt to gain access to networks and evade detection. However, the growth of CaaS means that there will continue to be a high volume of increasingly sophisticated attacks—and more new variants—for security teams to contend with.
To protect against cybercriminals’ growing list of tactics, organizations must focus on consolidating their security technology, reducing the number of vendors they work with to remove complexity from day-to-day operations. In the face of a growing threat landscape, security teams should also consider working with a trusted third party to conduct incident response and readiness activities—like developing playbooks and conducting tabletop exercises—to ensure they’re prepared to defend the organization when an incident occurs.
More About the 2H 2022 FortiGuard Labs Threat Landscape Report
The latest Global Threat Landscape Report represents the collective intelligence of FortiGuard Labs, drawn from Fortinet’s vast array of sensors collecting billions of threat events observed worldwide during the second half of 2022. The FortiGuard Labs Global Threat Landscape Report uses the MITRE ATT&CK framework to describe how threat actors find vulnerabilities, build malicious infrastructure, and exploit their targets. The report covers global and regional perspectives.








