2 mins read
April 19, 2024
April 19, 2024
Copyright 2023, IT Voice Media Pvt. Ltd.
All Rights Reserved
 Bitcoin Digital signature with its verification is main key factors behind the Bitcoin protocol.
Bitcoin Digital signature with its verification is main key factors behind the Bitcoin protocol.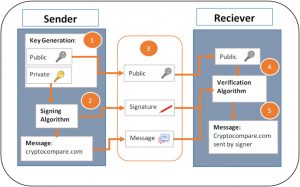 Using elliptic curves and their properties the signer, or sender, creates three points – remembering that the Bitcoin curve is defined as below:
Using elliptic curves and their properties the signer, or sender, creates three points – remembering that the Bitcoin curve is defined as below: