ITVoice News: We have just learned about BadUSB vulnerability. The report was publicly announced at Black Hat conference in Las Vegas by Karsten Nohl and Jakob Lell. Until researchers fix this vulnerability, the best advice is to avoid using non-credible USB drives from strangers.
 These German researchers demonstrated the working utilize, in one example. They used USB stick which made the system believe that it was keyboard. The USB stick automatically started typing commands, it triggered the PC to download malicious softwares from the Internet.
These German researchers demonstrated the working utilize, in one example. They used USB stick which made the system believe that it was keyboard. The USB stick automatically started typing commands, it triggered the PC to download malicious softwares from the Internet.
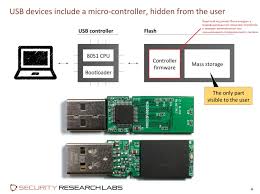
Every USB stick has a controller chip inside it. This chip is very easy to program and fill with malicious software. According to the report by SRL (Security Research Lab), a system infected by BadUSB is bricked, this security exploitation can spread very rapidly. Nohl believes that this problem is unpatchable.
A report from SRL states that, a BadUSB interferes directly with the core system, it can completely replace the BIOS of the computer. It is ineradicable malware. Infected computer and USB ports can infect the normal USB stick upon connecting. Reinstalling the operating system is the only solution if your system gets affected by BadUSB.
Few days ago, Adam Caudill and Brandon Wilson have released the code that can exploit the USB sticks. These researchers have made the code available on GitHub. The code is reverse engineered firmware for microcontroller chipset in USB sticks. They’ve reprogrammed the microcontroller to perform attacks.
Caudill and Wilson made this public announcement at Derbycon Conference, which happened at Louisville in last week. They said, “The information to fight against this vulnerability should be available to the public, we have released everything that we have studied, researched and found on GitHub. Our code will prove that USBs are impossible to secure. It is very tough to make it easy for people to do it on their own. We want to be on the right side ethically. We are doing this with the hope that making working exploit available publically will force USB stick manufacturers to change the structure and security of existing USB sticks.”
According to the article by Wired, the code published by Caudill and Wilson works only with firmware of USB 3.0 sticks by Phison company from Taiwan. This code patch has number of limitations. Manufacturers can modify physical access of firmware by ‘pin shorting’.





