CloudSEK researchers discovered several freemium SaaS platforms that scammers abuse to conduct phishing campaigns against popular companies. Most of these campaigns targeted Indian banking, financial services, and insurance (BFSI) customers.
Threat actors have resorted to using legitimate SaaS (software as a service) platforms to host phishing pages at a minimal/ no cost. These short-lived and easy-to-host phishing pages are also difficult to trace back to the actors responsib
SaaS (Software as a Service) products and services usually offer free or low-cost trials. While this has allowed users across the world to try out services before subscribing or buying the products, it also provides an opportunity for threat actors to pose as legitimate users and misuse the products to defraud consumers.
CloudSEK’s TRIAD identified several such incidents, especially targeting banking customers, and released advisories to inform the affected SaaS companies and the public.
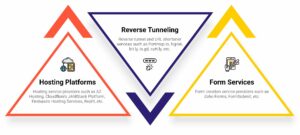
Scammers were able to evade detection by cleverly exploiting the following user-friendly services provided by each of these platforms.
*Note: All the SaaS companies mentioned in the report are legitimate and are not responsible in any way for threat actors abusing them. Additionally, some companies like Zoho even have a disclaimer that explicitly warns users against sharing credit card details and other sensitive information.
Hosting Platforms
Hosting platforms allow users to build and manage websites that are accessible via the Internet. Threat actors operating phishing campaigns often utilize the services offered by various web hosting platforms to create phishing pages.
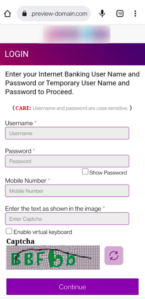
By creating these phishing websites, scammers are able to evade detection and steal individuals’ net banking credentials as well as PII information such as Aadhar card, PAN card, etc. This technique is particularly interesting as it can be challenging to classify the links before a campaign begins on a large scale, as many of them may not be available on the Internet.
In 2022, CloudSEK TRIAD conducted an in-depth analysis of 300 such domains out of which 40 domains were hosted using A2 Hosting’s temporary domain functionality and 260 domains were hosted using Hostinger’s preview domain feature.
Abusing Developer-Friendly Features
Cybercriminals always try to use free services for phishing campaigns to maximize their profits. Developer-focused platforms like Cloudflare Pages and Firebase Hosting provide certain features such as GitHub integration, which are easily abused to create phishing domains. In these campaigns also the main motive of the scammers remains the same, i.e. stealing sensitive banking information or PII and then using this information to generate fake KYC accounts or to carry out fraudulent activities via pretexting or vishing techniques.
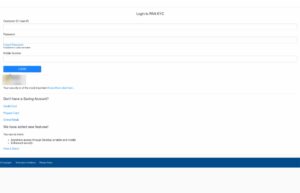
In 2022, CloudSEK TRIAD conducted an in-depth analysis of 57 such domains targeting the BFSI sector and over 200 domains targeting Netflix and Amazon.
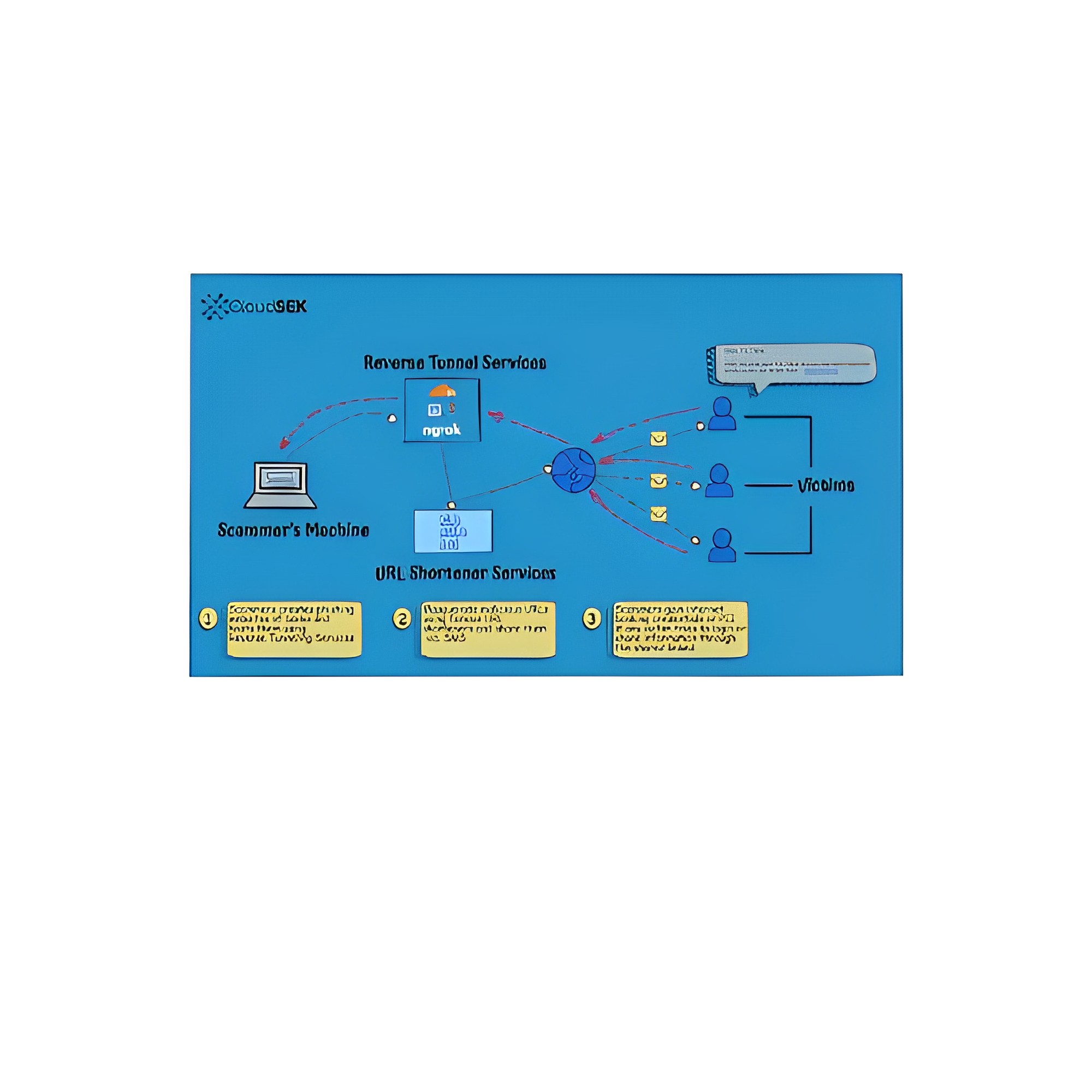
Reverse Tunneling Service Providers
Reverse tunnel services like Ngrok, LocalhostRun, Portmap.io, Try CloudFlare enable threat actors to expose their local server ports to the Internet and serve malicious content to customers.
Reverse tunnel services usher in a new era of phishing by making it easier for threat actors to stay under the radar. Threat actors can host phishing pages from their local machine and generate URLs with random names that cannot be detected by regular domain name scanning services. Whereas URL shorteners can further obfuscate the random domain names and evade detection. Since these URLs stay live only for 24 hours, it becomes difficult to track groups and their activities. There are no policies that mandate the reverse tunnel service providers to monitor or takedown malicious URLs. Hence, these have become an attractive channel for threat actors to launch large-scale campaigns.

Tweet from the customer complaining about a phishing website
Form Services
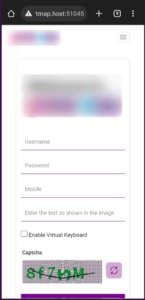
SaaS platforms such as Zoho, FormSubmit, etc., provide no-code form creation services which are designed to send input data from an HTML form straight to a specified email address. During the routine security scans, XVigil discovered a Twitter account involved in a new type of phishing campaign where scammers were misusing Zoho Forms to steal confidential information from banking customers.
Further investigation into the incident revealed a series of phishing campaigns operating on a similar modus operandi, as shown below.

Phishing campaigns operated in this manner majorly exploited form services provided by Zoho Form and FormSubmit, primarily to target banking customers. These forms were designed to look legitimate and trick people into entering their PII, such as their name, address, and financial information.