
 BANGALORE, India – May 28, 2013
BANGALORE, India – May 28, 2013
Dr.WEB, Russian developer of information security software, has studied one of the most widespread threats in April 2013, the Trojan Trojan.Mods.1, formerly known as Trojan.Redirect.140. According to statistics compiled by the curing utility Dr.Web CureIt!, the number of infections with this Trojan represent 3.07% of the total number of detected threats. A summary of the study can be found below.
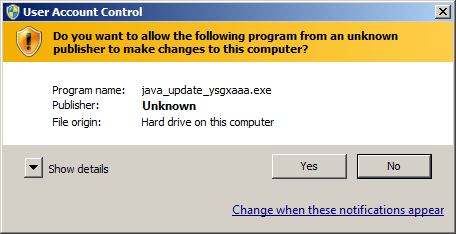
Then the dropper saves on the hard drive the main library which injects its code into all running processes on the infected computer but operates only in the processes of the following browsers: Microsoft Internet Explorer, Mozilla Firefox, Opera, Safari, Google Chrome, Chromium, Mail.Ru Internet, Yandex.Browser, and Rambler Nichrome. The configuration file containing all the data needed to run Trojan.Mods.1 is encrypted and stored in the dynamic linking library.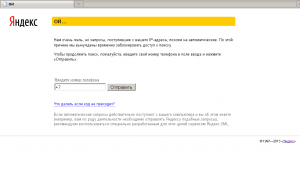
Trojan.Mods.1 is chiefly designed to replace web pages visited by users with malicious web pages by intercepting the system functions responsible for translating DNS names to IP addresses. As a result, instead of the sites they have requested, users are redirected to fraudulent pages where they are asked to enter a mobile phone number and reply to an SMS sent from the short number 4012. If they comply, a certain amount will be debited from their account.
The architecture of Trojan.Mods.1 contains a special algorithm that allows redirection to a certain group of addresses to be disabled.
The signature of this threat has been added to the Dr.Web virus database, so Trojan.Mods.1 does not pose a serious threat to systems protected by Doctor Web products.





